Automated Secret Expiration for Azure using Azure Logic Apps and Microsoft Graph
The Problem
In large organisations there can be hundreds if not thousands of applications registered to Azure Active Directory, with different secrets expiring at different times, when following best practice these secrets will be expiring regularly. Manually tracking the expiry is a massive pain, and waiting for them to expire is not an option.
The Code
Want to skip straight to the good stuff? Just deploy the code using the button below or view the source on Github using the second button!
The Solution
An automation to regularly check the upcoming expiry, that emails you a list of secrets and highlights those soon to expire. This Azure Logic App build on the great work by Russ Rimmerman which you can find here. I have modified the logic in the app to use managed identities instead of client secrets (one less secret to manage!). I have also replaced the ‘Send Email V2’ function with a call to Microsoft Graph using the ‘Mail.Send’ permission, which makes this dead simple to deploy across multiple tenants.
The Tools
- Azure Logic Apps
- Microsoft Graph
- Azure Cloud Shell (PowerShell)
Azure Logic Apps are a great way to repeatedly deploy cost-effective automation. They are very powerful along with being cheap and relatively simple to build.
Microsoft Graph Microsoft Graph is the unified API endpoint for all things Microsoft - it is the new standard and very portable only requiring HTTP requests.
Azure Cloud Shell Available on any web browser and comes with the Azure AD PowerShell module pre-installed.
Deploying the Logic App in your tenant
The easiest way to deploy this logic app in your tenant is to use the “Deploy to Azure” button above The Code
When presented with the below screen, select your resource group or create a new one. The highlighted fields can be modified to suit your own needs.
- Logicappname - change the default if you don’t like it.
- Sender_email_address - choose the mailbox you will send the report from.
- Recipient_email_address - choose the mailbox that will recieve the report.

Create the resource. Once its deployed there is one more step, to add the permissions.
Head over to the deployed logic app, under Settings Identity make note of the Object (principal) ID, this is the object we will be assigning the permissions to.
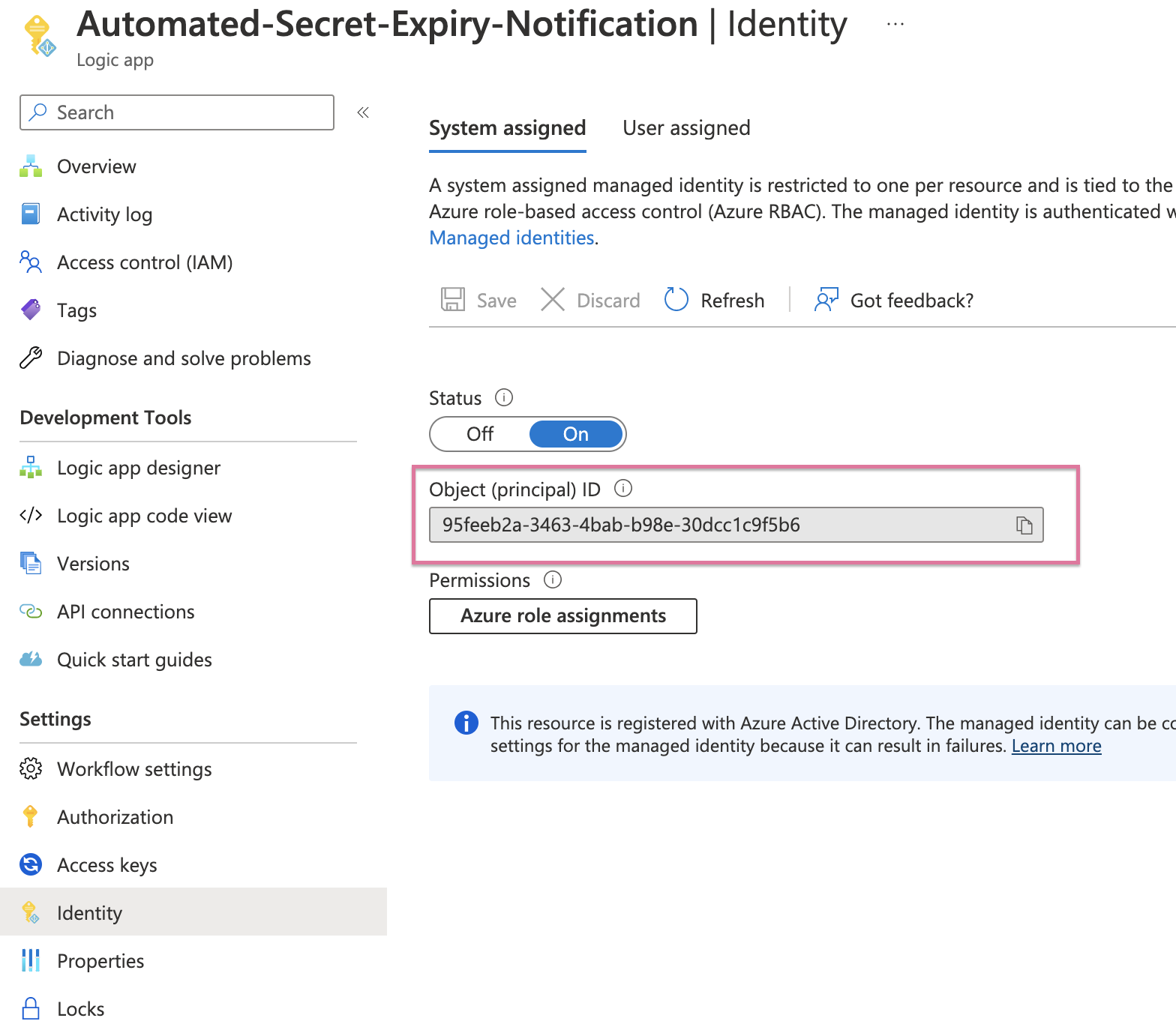
Adding the permissions
The final step is adding the permissions to the managed identity, this is what allows the logic app to call the Microsoft Graph API to get the application expiry and send emails.
The quickest way to do this is using Azure Cloud Shell and the Microsoft Azure AD PowerShell module.
Warning Notice: Microsoft is deprecating the Azure AD PowerShell module anytime after June 30th 2023 (source) in favour of Microsoft Graph as the preferred way to interact with Azure AD. This post adds the permission using Microsoft Graph, along with with other Infrastructure as Code (IaC) improvements.
Launch an Azure Cloud Shell and enter the following commands
Connect-AzureAD
$graphAppId = '00000003-0000-0000-c000-000000000000'
$ServicePrincipalID = [Enter the objectID saved earlier]
$graphApiAppRoleName1 = 'Application.Read.All'
$graphApiAppRoleName2 = 'Mail.Send'
$graphServicePrincipal = Get-AzureADServicePrincipal -Filter "appId eq '$graphAppId'"
$graphApiAppRole1 = $graphServicePrincipal.AppRoles | Where-Object {$_.Value -eq $graphApiAppRoleName1 -and $_.AllowedMemberTypes -contains "Application"}
$graphApiAppRole2 = $graphServicePrincipal.AppRoles | Where-Object {$_.Value -eq $graphApiAppRoleName2 -and $_.AllowedMemberTypes -contains "Application"}
New-AzureADServiceAppRoleAssignment -ObjectId $ServicePrincipalID -PrincipalId $ServicePrincipalID -ResourceId $graphServicePrincipal.ObjectId -Id $graphApiAppRole1.Id
New-AzureADServiceAppRoleAssignment -ObjectId $ServicePrincipalID -PrincipalId $ServicePrincipalID -ResourceId $graphServicePrincipal.ObjectId -Id $graphApiAppRole2.Id
Finished! If the permissions were applied successfully you should see an output like the below.

Warning Notice: The ‘Mail.Send’ Graph permission assigned here is extremely permissive, allowing for the application to send email on behalf of any mailbox in the tenant, this scope should be narrowed down and is covered in the next post.

